WHAT IS ARP (Address Resolution Protocol)
Most computer application programs use logical address (IP address) to send and receive messages, however the actual communication happens over physical address (MAC address) i.e from layer 2 of OSI model. So their job is to get the destination MAC address which helps to communicate with other devices. The image below is ARP, its function is to convert IP address to physical address (MAC).
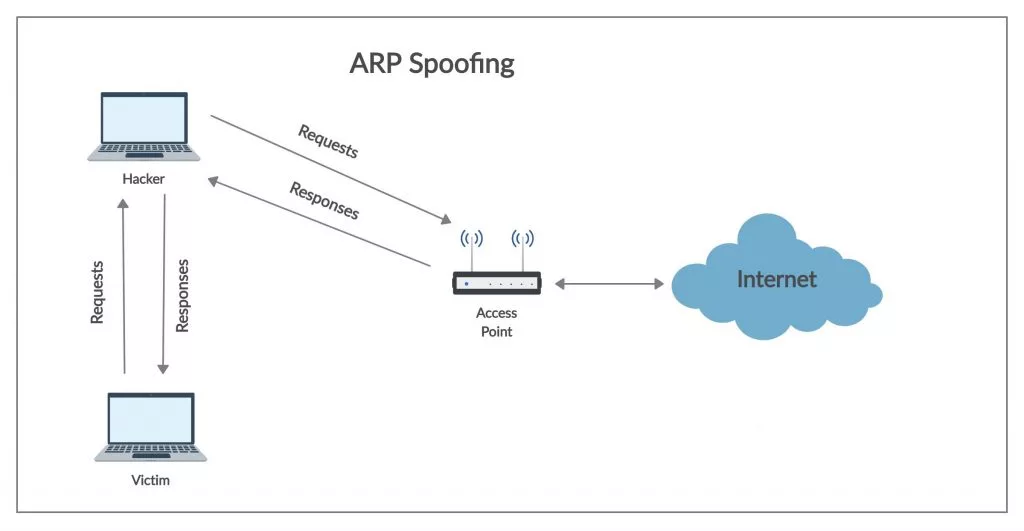
The attack would go like this:
1. The attacker must have access to the network. They scan the network to determine the IP addresses of at least two devices — let’s say this is a workstation and a router.
2. The attacker uses a spoofing tool, such as Arp spoofing or Driftnet , to send a spoofed ARP response.
3. The spoofed responses inform that the correct MAC address for both IP addresses, belonging to the router and workstation, is the attacker’s MAC address. This tricks both the router and the workstation into connecting to the attacker’s machine, instead of connecting to each other.
4. The two devices update their ARP cache entries and from that point on, communicate with the attacker instead of directly with each other.
5. The attacker is now secretly standing in the middle of all communications.
An ARP spoofing attacker pretends to be both parties to a network connection. When attackers spoof ARP, they can:
Continuing to route communications as they are, an attacker can sniff (sniff ) packets and steal data, except in cases where the packet is transmitted over an encrypted channel such as HTTPS.
Perform session hijacking , if an attacker obtains the session ID, they can gain access to the account the user is currently logged in with.
Change communication – for example, push a file containing a strange virus or malicious website to the computer .
DDoS attack – attackers can provide the MAC address of the server they want to attack with DDoS, instead of their own machine. If you do this for a large number of IPs, the target server will be hit by the traffic.
How to view ARP cache on windows
Go to cmd and type keywords: arp -a
Prepare
Hacker machine: Kali linux
Victim: Windows
File login spoofing ( http://demo.techsecurity.asia ) Contact Admin
Attack diagram.
Hackers will use network scanning technique to scan all devices in the network and use enumeration technique to list the ip and MAC addresses of all devices in the network.
First you have to logon the user as root (the highest permission kali ) here . After gaining root privileges, Execute the command to install ettercap as follows:
apt install ettercap-graphical
Here I will use ETTERCAP tool with GUI
Step 1. On the Kali interface, Open Command Line, type SU and enter passwd, then type ettercap -G command .
Select the tick as shown to display more features, pay attention to the functions as shown.
Here will show the process of Starting Unified sniffing
Step 2. Select the 3 dots and select Scan for hosts .
The result is a scan of 4 hosts added to the hosts list…
Step 3. Select hosts list to display the checked host list
Step 4. Select the PAUSE button to pause the starting process.
IP of victim machine: 192.168.157.128
IP Route: 192.168.157.2
Add to Target 1 for IP of victim machine:
Add to Target 2 for Route:
As shown (green circle)
Step 5. Select ARP poisoning
Select ok to Sniff remote connections.
Step 6. Tick the START button to start Unified sniffing
Step 7. Turn on Wireshark as shown
Step 8. Turn on Wireshark by selecting the blue button as shown
Step 9. View IP on Hacker machine: ifconfig , show ether port and MAC
Step 10. View IP Route, type command sudo apt install traceroute
traceroute 8.8.8.8 (show IP Route 192.168.157.2 )
Step 11. On the victim machine: ipconfig /all
Step 12. Go to the test website: ( http://demo.techsecurity.asia ) as shown. Enter any information
Step 13. PAUSE Wireshark , use http command to find information via POST /Login.php
Step 14. Select the line Hypertext Transfer Protocol . show password
Step 15. Verify the website is working properly, enter information:
username : demo
passwd : demo
CONCLUDE:
At this point, you can also imagine how Hackers attack victims with ARP Spoofing technique, right?. As you all know, if you don’t know how to prevent and prevent it in time before being attacked by hackers, what will be the consequences.
1st . Money scam: Fraud in the form of borrowing money, credit, unsecured, buying personal items, or scamming prey or texting or calling victims.
Second . Friend scam: Scamming friends with loose sentences, hanging pranks, borrowing convenience for further study, borrowing large amounts of money without paying. The victim has to shoulder the burden to pay the debt.
Third . Infomation icome: Disclosure of personal information such as Accounts and passwords, private information, sensitive images, etc.
Don’t worry, this article will guide you on how to prevent and prevent hackers from attacking us before the hacker takes action, so that we will no longer be knocked down by exposed sites like Facebook . , youtube , gmail …
How to prevent attack by hacker at coffee shop – Technical arp spoofing